CYBER AWARENESS :
What is Phishing and how you can be Safe!
Phishing is the fraudulent use of electronic communications to deceive and take advantage of users. Phishing attacks attempt to gain sensitive, confidential information such as usernames, passwords, credit card information, network credentials, and more. By posing as a legitimate individual or institution via phone or email, cyber attackers use a form of deceit known as Social Engineering to manipulate victims into clicking on a malicious link or attachment, and/or willfully divulging confidential information.
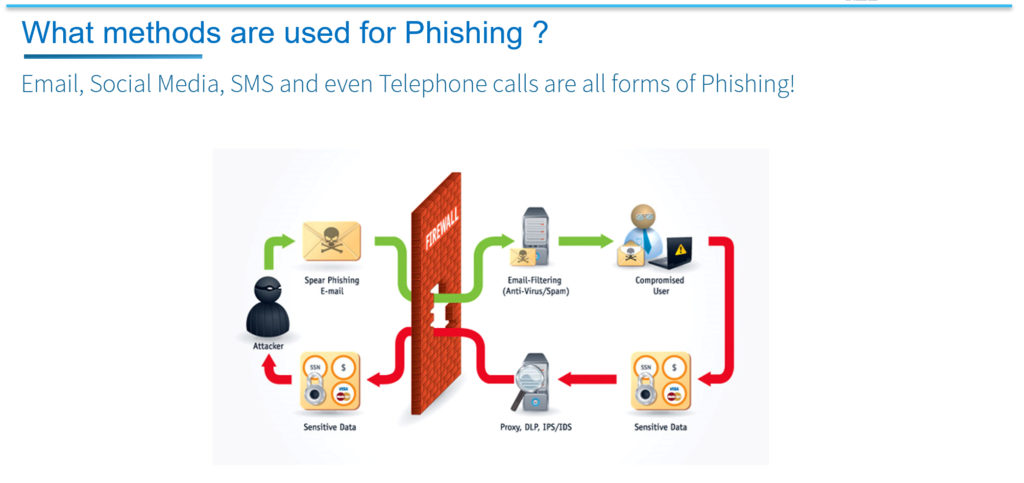
Phishing attacks most often begin with an email attempting to obtain sensitive information through user interaction, such as clicking on a malicious link or downloading an infected attachment. By this method, the attacker is able to get around, or through, the security that the company has enabled for protection. Firewalls for example used to be the security priority as they form the Boundary or the Fence for an organization’s internal systems. By clicking a link in a Phishing email, the firewall and all other security is bypassed allowing the attacker to assume your connection to internal systems. Attackers can also phone calls, text messages, and social media to Phish victims into providing sensitive and personal information.

Phishing attacks come in many various forms and types;
Spear Fishing – Where attackers take time to gather information about their targets to fill emails with more authentic context. Some attackers even hijack business email communications and create highly customized messages for a specific target.
Clone Phishing – Attackers are able to view legitimate, previously delivered email messages, make a nearly identical copy of it—or “clone”—and then change an attachment or link to something malicious.
Whaling – Whaling specifically targets high profile and/or senior executives in an organization. The content of a whaling attempt will often present as a legal communication or other high-level executive business.
It is recommended that organizations educate employees to prevent phishing attacks by recognising suspicious emails, links, and attachments. Cyber attackers are always refining and improving their techniques, therefore on-going education is critical to success.
Some tell-tale signs of a phishing email include:
- ‘Too good to be true’ offers,
- Unusual source,
- Poor spelling and grammar,
- Threats of account shutdown, and …
- anything conveying a sense of urgency,
Links, especially when the destination URL is different than it appears in the email content and
Unexpected attachments, especially .exe or .com files, however .doc and .xls can also be dangerous.
If you receive a suspicious email, attachment, txt or Social Media message, do not click links or open any attachments.



