It certainly wasn’t the biggest cyber hack in the world – although it was the biggest in Twitter history – but it most certainly was the most high profile!
Background: On July 15th 2020, several high profile celebrities had their Twitter accounts compromised in what appeared to be a broadly targeted Celebrity hack. The result was a series of similarly worded messages being posted on profiles asking millions of followers to send money to a specific bitcoin wallet address, in return for larger payback.
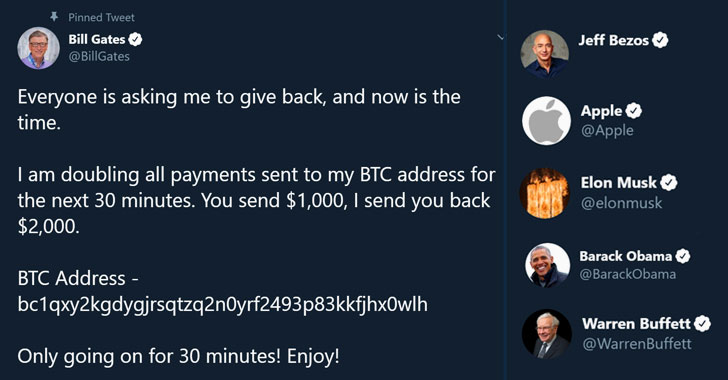
The message, displayed on accounts belonging to Barrack Obama, Joe Biden, Bill Gates, Elon Musk, Jeff Bezos, Apple, Uber, Kanye West, Kim Kardashian, Floyd Mayweather, Michael Bloomberg, as well as others, had asked users to send Bitcoin as a double-up investment.
“Everyone is asking me to give back, and now is the time,” a tweet from Mr Gates’ account said. “You send $1,000, I send you back $2,000.”
31st July, 2020: The USA Department of Justice (DoJ), posted reference documents in support of their arrest of three individuals charged with the Twitter Hack.
The charges were also mentioned in a Youtube video on the channel of the “Executive Office for United States Attorneys“.
In that announcement, it was stated that the Hack consisted of a number of Technical Breaches, as well as the method of Social Engineering.
The three individuals were identified in published documents as;
- Mason Sheppard, aka “Chaewon,” 19, of Bognor Regis, in the United Kingdom.
- Nima Fazeli, aka “Rolex,” 22, of Orlando, Florida.
- Graham Ivan Clark, believed to be “Kirk,” 17 of Tampa, Florida.
3rd May, 2020: According to the evidence at hand, the hack actually commenced much earlier than the penetration date and was in fact executed by Graham Ivan Clark, at that time a resident of California, when he accessed `a portion’ of the Twitter network on May 3rd, 2020.

Most Cyber forensics professionals know that typically, a hack is executed in a Vertical manner, ie North to South from the internet, which then moves Lateral, ie East-West, in pursuit of the payload. In this case, Clarke waited until July 15 to execute the hack, and in subsequent investigation we learn that Clark perhaps did not have the leverage that he wanted at the initial point of entry, to execute and maximize the hack.
According to reports in the Hacking Community, and as later reported in the New York Times, it appears that Clarke actually gained access to one of the internal Twitter Slack Channels and not to the Twitter system itself. In fact, it was reported that the hacker found authentication credentials to one of Twitter’s administrative tech support tools pinned to one of the Slack workspaces.
Below is a screenshot of Twitter’s back end tool which allowed employees total control of Twitter user’s account. In this case, the @R9 account.
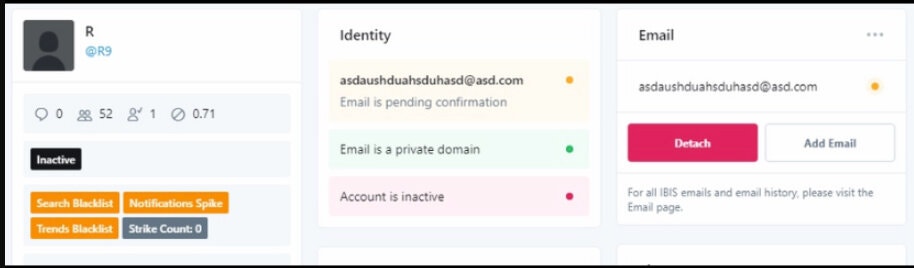
Although a great score, the credentials to this tool were still not enough to access the user’s account as Twitter’s administrative backend is protected by Two-Factor User Authentication (2FuA).
15th July, 2020: This is where Clark’s criminal mind went to work. According to Twitter investigative reports, on 15th July, the day of the hack, he used a “spear phishing attack” to trick some Twitter employees and gain access to their accounts, thereby defeating Twitter’s two-factor protection.
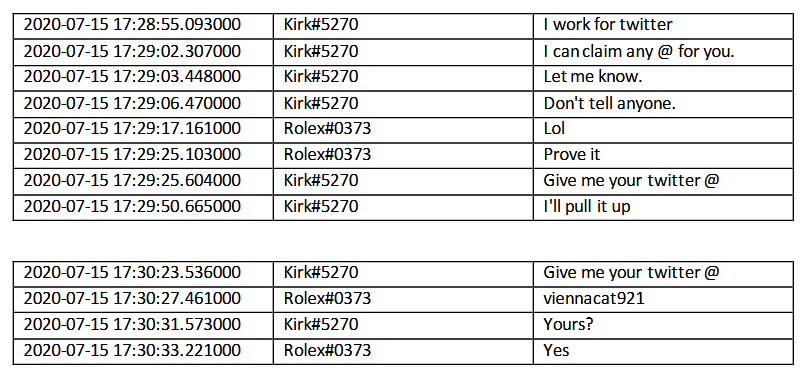
Clark was registered on the Chat site “Discord” where he was known by the handle “Kirk#5270”. Evidence supplied by the FBI included Chat Logs that indicated Clarke had contacted two other Discord users seeking assistance to convert his access into cash.
This is where Clark became connected to his two accomplices Nima Fazeli (known on Discord as “Rolex#037”) and Mason Sheppard (known on Discord as “anxious#0001”).
Clark’s approach was to convince Fazeli and Sheppard that he had admin access because he was a Twitter employee. Since he had access to Twitter’s Administrative tool, and had bypassed the 2FA, he easily proved his claims by changing settings on Fazeli’s personal account, and later sold him access to the account of another.
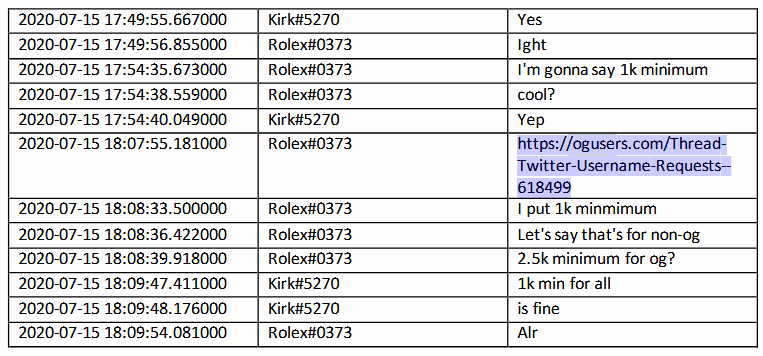
Clark was also able to sell Sheppard access to multiple short-form Twitter accounts, including @dark, @vampire, @obinna, and @drug.
At that point, the three collectively decided to promote Clark’s ability to hijack Twitter user accounts and posted a number of ads on the OGUsers forum pages with fees of “$1K” settled on.
These ads were successful in converting a number of people to buy access to Twitter accounts. Some of these are still being investigated by the FBI as further accomplices to the Hack.
Regardless, it was this access to celebrity verified Twitter accounts on this day of July 15, that allowed the subsequent posting of the cryptocurrency scam message.
According to court documents tendered, hackers operating Crypto wallets used in this scam received 12.83 bitcoin, equivalent to $USD117,000. A further investigation revealed that the quick thinking of cryptocurrency exchange Coinbase was able to block transactions which prevented a further $USD280,000 from reaching the destination wallet.
Of course once the message was displayed on the high profile accounts in unison, the hack became very public and known to the Twitter Cyber security team which reacted immediately to block Clark’s access.
Twitter later noted that during his access on this day, Clark accessed 130 accounts via the Twitter admin tool, initiated a password reset for 45, and accessed private messages for 36 accounts.
16th July, 2020: On this day, 24 hrs after the attack was identified by Twitter, the Social Giant lodged a formal incident report with the FBI.
The FBI, aided by the USA’s IRS, obtained data from Coinbase about the Bitcoin addresses involved in the hacks, and correlated these with the addresses used and mentioned by the three hackers on Discord chats and OGUsers forum posts.
A sequence of very simple mistakes then followed which allowed the FBI to locate the hacker identities, and link them to email and IP addresses.
Fazeli for example, had his Discord username linked to his OGUsers forum account.
According to a report mentioned on ZDNet, Fazeli then used the damniamevil20@gmail.com address to register an account on the OGUsers forum and the chancelittle10@gmail.com email address to hijack the @foreign Twitter account.
He also used the same two email addresses to register Coinbase accounts, which he later verified with a photo of his driver’s license. This was a Coinbase requirement in order to establish the destination wallet to receive the Crypto payments.
In the final error, Fazeli used his home internet service to access accounts on the three sites, leaving his home Public IP address in the access logs across all three internet webservices — Discord, Coinbase, and OGUsers.
Similarly, Sheppard (anxious#0001), who went on OGUsers as Chaewon, left clues for investigators who were able to connect his Discord user with his OGUsers account via the ad he posted on the day of the hack. They also connected other posts on the OGUsers database, where Chaewon bought a video game username with a Bitcoin address that was connected to addresses used on the day of the Twitter hack.
Just like in Fazeli’s case, Sheppard also used his actual driver’s license to verify his Crypto accounts. This is a standard requirement of Crypto exchanges.
31st July, 2020: At first, Clark was more difficult to link to the Kirk#5270 Discord user, however this concluded on 31st July with documents filed by US government sources.
Hillsborough State Attorney Andrew Warren claimed that Clark, the 17-year-old teen from Tampa they arrested on this day, was in fact the “mastermind” of the entire hack, which is the role played by Kirk#5270 in the scheme.
Additionally, a statement released on this day by the Northern District of California, referred the third hacker, a juvenile, to the State Attorney for the 13th Judicial District (Hillsborough County) in Tampa, Florida.
The same Florida office then announced the hacker’s arrest and revealed his real name as Graham Ivan Clark.
Conclusion: It could be considered that the downfall of the hackers was a combination of naivety of youth leading to errors, well balanced security requirements of Coinbase, and the investigative talents of the FBI. It still remains however, that a very simple and common indiscretion by an employee to place the login credentials on a company Slack Workspace, was the beginning of a well executed hack. Known as a Back-Door Attack and accompanied by a Social Engineering and Spear Phishing Campaign, the entire userbase of Twitter became available very quickly to the attackers. Many companies base their claims of security in the faith of a particular technology or tool. The Twitter Hack demonstrates that these can be overcome and that true security requires an intelligent strategy of extensive cultural and behavioral uplift as well as a good technology solution.





2 Responses